Kernel Basics¶
The kernel is a program that runs with full access privileges to the entire computer. The kernel controls access to all shared system resources, including physical memory, the file system, and I/O devices. The kernel is also responsible for handling all exceptional system and software events, such as power disruption or the addition of new “plug-and-play” peripheral components. To be precise, the kernel is primarily responsible for two functions. It acts as a resource manager, providing access to shared system hardware resources as needed. The kernel also acts as a control program, handling errors and access violations in a safe manner.
The origins of the kernel date back to the earliest days of mainframe computing, when it was known as the monitor. The monitor was a collection of software routines for standard operation that got included with every program when it was run; these included routines for clearing out memory and loading stored data. The term was later changed to resident monitor to reflect the fact that this code was always present (resident) in memory.
In the family of x86 architectures, the CPU’s operating mode is stored as a 2-bit value known as the current privilege level (CPL), which is also called a ring. Although these architectures make it possible to have four rings, only two are used in practice. When the system is in ring 3 (user mode), the set of instructions that are allowed is restricted and no instruction can access any part of memory owned by the kernel.
In ring 0 (kernel mode), all valid memory addresses can be accessed and an additional set of privileged instructions can be performed. Examples of privileged instructions include hlt, which halts the CPU, and invd, which can be used to invalidate the CPU cache. In addition, some normal instructions behave differently in ring 0 than they do in ring 3; popf (pops a word from the stack into the status flag register) is one example, as some status bits are not updated in ring 3.
To further illustrate the distinction between the kernel and the common usage of the term OS, consider the notion of OS versions or distributions. Windows users are probably familiar with names such as XP, Vista, or Windows 10.
Note
Similarly, Mac users might distinguish macOS Sierra or OS X El Capitan, just as Linux users may talk about Linux Mint, Ubuntu, or Red Hat Linux.
In all three of these cases, all of the versions and distributions share a common kernel. In the case of Windows, the kernel is known as the NT kernel, which was first released in 1993. macOS is the most recent name of the Mac OS X kernel, which was first released in 2001. All distributions of Linux use the Linux kernel, which was first released in 1991. The various OS distributions are primarily distinguished by the non-kernel programs and services that are included. Although the kernel may contain some updates, the internal structure and services have remained moderately consistent.
Kernel Memory Structure and Protections¶
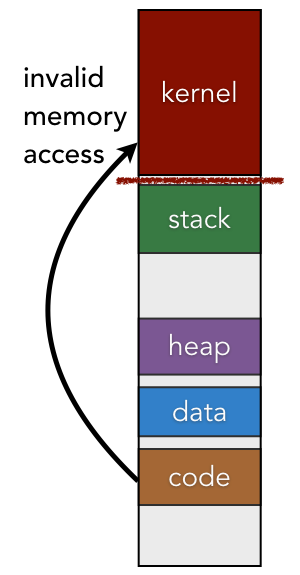
The kernel exists as a protected region of virtual memory within the context of every process. Just like a normal user-mode program, the kernel contains a code segment, global data, and a heap for dynamic memory allocation. Rather than having a single stack, however, the kernel contains many stacks; for each user-mode process, the kernel contains at least one stack.
In general, the kernel interacts with its memory regions the same way as normal programs interact with theirs. The CPU uses the %rip register to load the next instruction from the code segment. Dynamically allocated data structures are stored on the heap and local variables are stored on the stack that is currently in use.
Since the kernel contains information about all processes and system resources, user-mode programs must be prevented from tampering with it. For instance, you would not want a faulty program to reformat your hard drive or shut off power are random times; only the kernel should be able to perform these actions. To prevent tampering from other programs, the kernel configures the CPU to restrict access to the portions of physical memory that are storing the kernel’s virtual memory contents. As a result, if an instruction tries to access a memory location within the kernel while the CPU is set to user mode, the CPU itself will detect this invalid access and trigger an exception.