4.7. Application-Layer Broadcasting: DHCP¶
DNS provides a mechanism that clients can use to determine the IP address for a server based on a
human-readable domain name. In addition, server processes for common protocols listen for incoming
requests on well-known ports. The client can use the address and port number to call connect()
to establish a TCP connection for an HTTP request; for UDP services like DNS, the client uses the
address and port number when it calls sendto() to deliver the datagram. Thus, in both cases,
there are clear mechanisms for how the client determines the IP address and port number for the
server. This raises the question of how the server determines the corresponding information to send
the message back to the client.
One part of the answer to this question is that the TCP and UDP services provide this information along with the request. As we will note in the next chapter, transport-layer protocols attach a header to application-layer data containing the IP address and port numbers for both the sender and the receiver. However, this answer is not fully satisfying, because it does not explain how the client’s IP address is set. (Explaining the port number is easy: For ephemeral ports, the OS picks a random 16-bit number, typically above the value 4096.)
IP addresses can be either static or dynamic. With a static IP address, the ISP determines a constant value that gets persistently associated for a particular device; the device is configured so that it uses the same IP address every time it boots up. Static IP addresses are commonly used for servers; this practice reduces strain on the DNS, which would have to be updated every time the IP address for a server changed. For end-user client devices, such as laptops, tablets, mobile phones, or Internet-connected smart home devices, IP addresses are normally determined by the Dynamic Host Configuration Protocol (DHCP), a protocol that assigns IP addresses dynamically when the device connects to a network. Note that this protocol is used in both wireless and wired networks, as DHCP will also run when a computer is connected via an Ethernet cable.
4.7.1. DHCP Overview¶
The specification for DHCP is defined in RFC 2131. The full protocol is significantly more complex than either HTTP or DNS, because DHCP requires multiple steps rather than the basic request-response structure. DHCP message exchanges can include negotiation back and forth between the client and server based on the hardware and software requirements of each. Additionally, clients can abort the request before the protocol completes, and the server would need to recognize when this happens and close the connection to free up resources. Implementing the full specification requires building state machines for both the client and server. In this section, though, we limit the discussion to the most basic type of (successful) exchange because it illustrates a new socket programming technique not discussed previously: broadcasting.
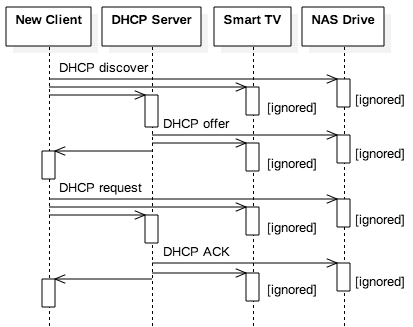
Figure 4.7.1 illustrates the sequence of messages across a network for a DHCP
request. To initiate a DHCP request, a new client (such as a laptop) uses UDP to broadcast a DHCP
discover message, which declares that the sender is trying to find a DHCP server. In other words,
the client sends a message using a reserved IP address that indicates the client does not know the
destination. If the client is connected to a router that is running a DHCP server, the router would
accept the message and would not forward it. However, if there is no intervening router (e.g., the
client is connected via an Ethernet cable), then the message is sent to all hosts on the local
network. Most devices on the network are not running DHCP servers, so they have no process listening
at the well-known DHCP port number (67). For instance, a connected smart TV or network-accessible
storage (NAS) hard drive would not be listening for incoming DHCP requests. For these devices, the
OS simply ignores the message.
When the broadcast message is received by a DHCP server, the server replies by broadcasting a DHCP
offer that informs the client of the server’s IP address, as well as proposing an IP address for
the client to use. If there are multiple DHCP servers running on the network, then any that receives
the DHCP discover message will respond with a DHCP offer. The client accepts the offer by
sending a DHCP request. Although this message is broadcast, the body of the request contains
information to designate which DHCP server’s offer is being accepted. That server confirms the
configuration to all devices by broadcasting a final DHCP ACK (acknowledgement) that declares
the new client has successfully been assigned to that particular IP address.
4.7.2. DHCP Protocol Messages¶
| 0-7 | 8-15 | 16-23 | 24-31 |
|---|---|---|---|
op |
htype |
hlen |
hops |
xid | |||
secs |
flags |
||
ciaddr | |||
yiaddr | |||
siaddr | |||
giaddr | |||
chaddr (16 bytes) | |||
sname (64 bytes) | |||
file (128 bytes) | |||
options (variable) | |||
Table 4.10: Structure of a DHCP message
RFC 2131 defines the core structure of DHCP messages, which is shown in Table 4.10. In this illustration, each row of the table is 32 bits (four bytes) wide, and some fields would require multiple rows, as they are larger than four bytes in size. While this structure shows the relative ordering of the fields, the exact structure depends on the type of message. Depending on the type, some fields may be required, others are optional, and still more are not allowed. RFC 2132 specifies the allowable options.
For the four basic messages shown in Figure 4.7.1, the important fields to consider
are op, xid, yiaddr, and siaddr. The op field can be set to either
BOOTREQUEST (1) or BOOTREPLY (2), indicating if the message is coming from the client or the
server. As in DNS, the xid is a random integer to denote the transaction ID, connecting replies
with the specific requests. The yiaddr is used to indicate your (the client’s) IP address,
while siaddr is the DHCP server’s address. The other fields, described in the RFC, are beyond the
scope of this book. Table 4.11 shows the values of these fields for a sample DHCP
request. All messages are sent to the destination IP address 255.255.255.255, which is the reserved
value that indicates a broadcast message. The client uses 0.0.0.0 as its source address for the UDP
messages, indicating the sending host has no valid address, while the DHCP server can use its own address.
The client distinguishes itself from other new clients by picking a random value to use as the
xid, which is 42 for the DHCP discover message in this case; after the server replies with
the same xid value, the client and the server repeat the same value again in the later messages. A
DHCP discover message from another new client might have 587 for its xid. By receiving a
broadcast message with xid 42 from the server, the client that started with 42 has
reasonable assurance that it is the intended recipient.
| Message type | UDP addressing | DHCP contents |
|---|---|---|
DHCP discover |
SRC: 0.0.0.0:68 |
op: BOOTREQUEST |
DHCP offer |
SRC: 192.168.1.1:67 |
op: BOOTREPLY |
DHCP request |
SRC: 0.0.0.0:68 |
op: BOOTREQUEST |
DHCP ACK |
SRC: 192.168.1.1:67 |
op: BOOTREPLY |
Table: 4.11: Structure of DHCP messages to set up an IP address
The other fields in the DHCP message establish the new client’s IP configuration. When the server
sends the DHCP offer, the yiaddr field contains a proposed value for the client’s address.
The client could reject the address, but here we assume that the offer is accepted. The client
indicates that it accepts the offer by using the same value in its DHCP request, and the server
confirms the acceptance in the DHCP ACK. In addition, these messages establish that the client
knows the IP address of the DHCP server (siaddr), along with the duration of the
lease—the time during which the client owns this IP address. In this case, the client will
have a lease on the address 192.168.1.7 for a maximum of 86,400 seconds (24 hours). When the lease
expires, the client would contact the server to renew the lease. At that point, the client would not
need to repeat the full protocol; since the client knows the IP address of the server, it does not
need to begin back at the DHCP discover stage.