
Create a use case diagram for this system.
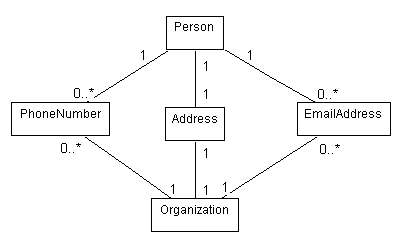
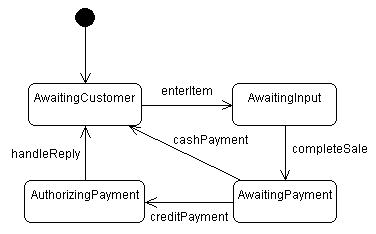
JMUmble. In this
system, arriving messages are handled by a PostOffice
object. Depending on how the system is configured at runtime, one or
more objects might need to know when a message arrives. I have
currently implemented several such classes:
ScreenFlasher (which makes the entire screen flash --
you always know when a message has arrived),
PopularityTimer (which starts a clock that show the
amount of time since the most recent message arrived), and
Mumbler (which uses speech generation to read the name
of the person that sent the message -- this is where the system got
its name). Use the observer pattern to develop a class model of
this system (in UML). You do not need to include the attributes of
each class, only the operations/methods. Include comments that
describe each operation/method.
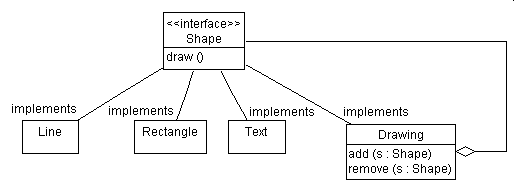
Implement the Drawing class in either Eiffel, C#, C++, Java,
or Smalltalk. (Note: You may work at a computer when answering this
question. That is, you may edit, compile, and execute your code
before you "submit" it.)
public static int calculate(int x, int y)
{
int a, b;
do
{
a = 1;
if (x > y)
{
a = 2;
}
x++;
b = x * a;
}
while (b <= 0);
return b;
}
Develop a set of test cases that will test every path through this method.
// Details omitted
a = in.nextInt();
b = in.nextInt();
c = a/b;
where the nextInt() method will return the next integer
value in the input stream associated with in.
Year Cost
1 3,000,000
2 2,700,000
3 1,200,000
4 5,100,000
5 8,000,000
The other plan requires eight years to complete and has the following
annual costs:
Year Cost
1 1,500,000
2 1,500,000
3 1,000,000
4 2,400,000
5 500,000
6 1,500,000
7 1,500,000
8 2,100,000
9 6,000,000
10 2,000,000
Calculate the present value of each of these two cost streams assuming a discount rate (i.e., interest rate) of 7 percent and that all costs are incurred at the end of the year.
Time
Task Required Dependencies
1 6
2 5 1
3 2 1
4 6 1
5 4 2,3
6 1 4
7 2 4
8 4 4
9 3 2
10 4 5,6
11 1 7,8
12 4 9,10
13 2 6,11
14 1 12,13
Copyright 2008